Week 9: Vulnerability Management
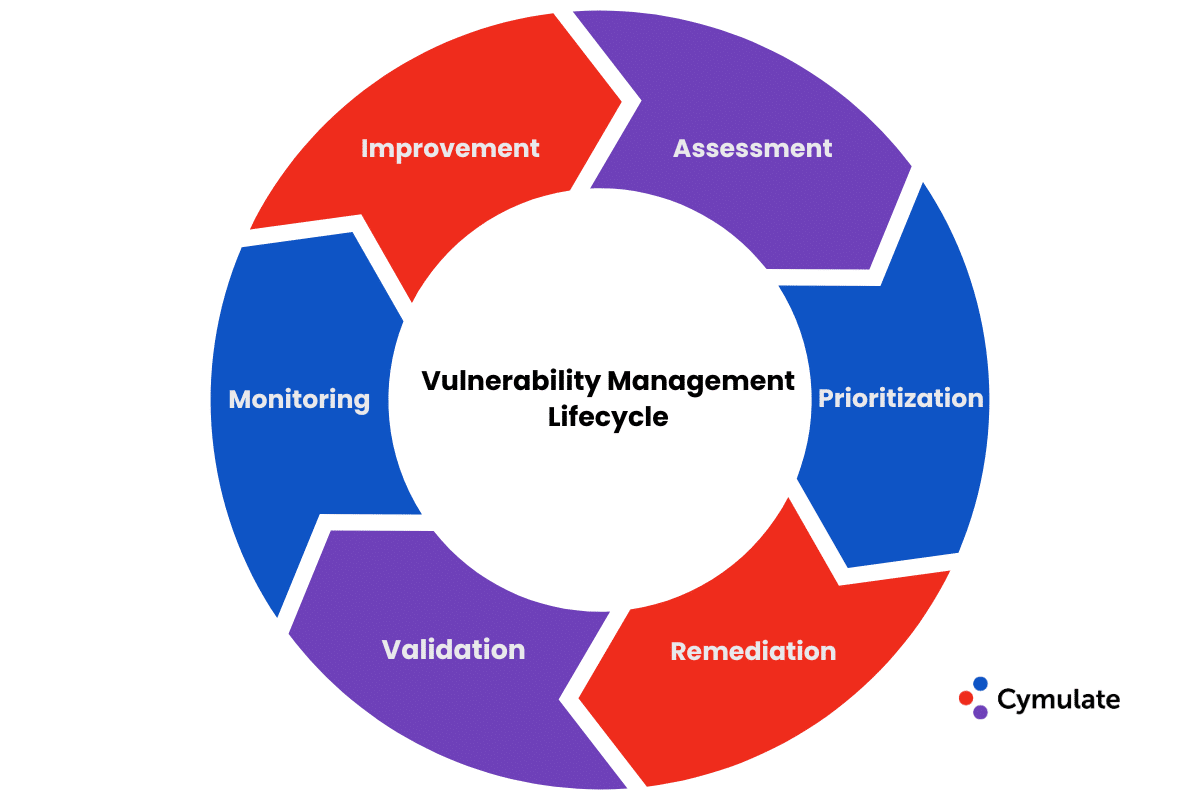
Vulnerability management is a continuous process that identifies, evaluates, treats, and reports security vulnerabilities across systems and software. It helps reduce the attack surface and ensure compliance. The process includes asset discovery, vulnerability scanning, risk prioritization, remediation, and verification. Automation and risk-based tools enhance its efficiency, making it essential for modern cybersecurity strategies.
Key Stages (Lifecycle)
-
Asset Discovery
Identify and catalog all IT assets—servers, endpoints, apps, networks—which forms the foundation for vulnerability scanning. -
Vulnerability Scanning
Use automated tools to detect known flaws such as misconfigurations, open ports, and out-of-date software across the infrastructure . -
Prioritization & Risk Rating
Assign risk levels (e.g., CVSS scores, severity ratings) based on likelihood, business impact, exploitability, and compliance requirements.. -
Remediation & Mitigation
Apply patches, adjust configurations, use compensating controls, or accept low-risk vulnerabilities; remediation workflows guide these actions. -
Verification (Reassessment)
Re-scan and monitor systems post-remediation to confirm issues have been resolved and to detect new vulnerabilities. Reporting & Compliance
Maintain dashboards, compliance mappings, and audit trails to track progress, performance metrics, and align with regulatory standards .Core Objectives
-
Shrink the attack surface by proactively identifying and resolving vulnerabilities.
-
Boost security posture through regular scanning, prioritized remediation, and tracking via dashboards.
-
Meet regulatory requirements like HIPAA, PCI‑DSS, and others requiring vulnerability management capabilities.
Vulnerability management isn’t a one-off initiative—it’s a cyclic process that adapts to evolving threats, changing infrastructure, and emerging risks. Staying ahead of attackers requires ongoing vigilance and refinement.
Resources: https://www.techtarget.com/searchsecurity/definition/vulnerability-management
Comments
Post a Comment